What motivates an individual to steal intellectual property from an organization? What types of employees are most likely to commit IP theft? How do they pull it off? And, most importantly, can they be detected and stopped by the security team before something bad happens?
CYDERES, the security-as-a-service division of Fishtech Group, thinks the answer to the last question is yes. But to succeed, the security team must first have a detailed understanding of the Who-What-When-Why-How of IP theft.
An excellent resource for understanding insider threats in all their various forms was published nearly decade ago, when researchers at Carnegie Mellon University’s Computer Emergency Response Team (CERT) Coordination Center published The CERT Guide to Insider Threats: How to Prevent, Detect, and Respond to Information Technology Crimes (Theft, Sabotage, Fraud).
The CERT authors delved deeply into the actions, attitudes and intentions of different kinds of insiders and came up with useful insights that have admirably stood the test of time. Along with the contributions of other experts in the field, these insights have influenced the design of our insider threat mitigation solutions and services.
Below is a summary of CERT’s profile of an IP thief.
- Who: Insiders who steal IP are usually current employees who are scientists, engineers, software programmers and sales personnel. The widespread perception that system administrators are among the biggest culprits, CERT found, is not supported by the research results.
- What: These individuals steal information they worked on directly, such as proprietary software and source code; business plans, proposals and strategic plans; customer information; and product information such as designs, formular and schematics.
- When: CERT found that most insiders stole at least some information within 30 days of resignation. That time frame actually encompasses a 60-day window: 30 days before leaving and 30 days after having left.
- Why: The reasons behind stealing IP can vary widely. One-third of IP thieves are looking to start their own business. Another 40% are starting a new job at a competing business. Most of the remainder represent instances of foreign governments or organizations compromising or enticing insiders to gain access to technologically- or commercially-valuable IP. Interestingly, according to CERT, very few insiders steal intellectual property in order to sell it. Rather, they seek business advantage.
- How: Exfiltration of intellectual property follows one of several tried-and-true pathways, including email, USB drives and removal of physical documents.
For companies worried they may have an IP theft problem but hesitant to launch their own insider threat program, CYDERES provides a range of capabilities through our first of its kind Insider Threat Detection & Response (ITDR) managed service.
ITDR analyzes an organization’s existing trove of user and network telemetry to find clues that an employee is behaving in a potentially adverse manner. It then uses operationally proven AI-based modeling techniques to filter out the excess noise from the data to identify the riskiest players, including IP thieves.
Buried in that telemetry is a wealth of intelligence on the insider’s circumstances and actions, which are an ideal proxy for gauging intent. The probabilistic model underlying our ITDR analytics turns each data point into a model concept and then builds a Bayesian inference network (image below) that captures the relationships between each concept as well as the relative strengths (low/medium/high) and polarities (true/false) between them.
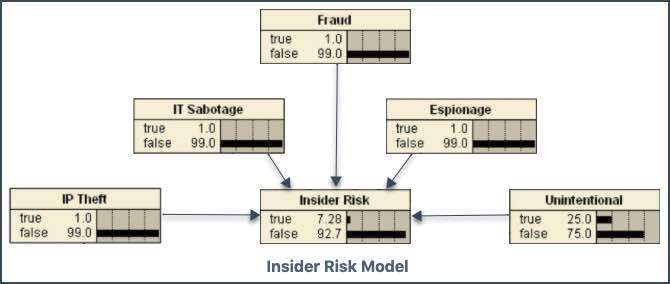
In simple terms, ITDR applies diverse data sources to the model. The data contains indicators of impactful personal or professional events plus a record of day-to-day actions – such as accessing the web or sending an email – and uses the results to assess and prioritize risk from an individual.
There are separate model indicators for behavioral characteristics, network and device activity and more. For the risk modeling component addressing use cases for ‘IP Theft,’ the strong indications relate to financial stress or impending threats to continued employment.
Medium-strength indicators can range from unwillingness to comply with established rules and procedures to anti-malware alerts. Low-strength indicators include an active social media presence or database content changes.
Our CYDERES Cloud Native Analytics Platform (CNAP) ingests the model results and a CYDERES analyst validates and triages them, delivering the results to organizations in the form of detailed incident alerts and the related evidence needed to launch an investigation, comply with legal and audit requirements associated with such activity and enhance future risk mitigation via policy and control changes.
Because it is a managed service, ITDR can be implemented far more quickly than conventional insider threat mitigation solutions, meaning organizations can start mitigating risk via their employees and contractors much sooner.
The Commission on the Theft of American Intellectual Property estimates that annual costs from the loss of IP range from $225 billion to $600 billion. And the 2021 edition of Verizon’s widely respected Data Breach Investigations Report (DBIR) says that around 22% of such incidents are attributable to an assist from or the unilateral act of a trusted insider.
Industry sectors most often targeted, according to a separate CERT blog post, are information technology (35 percent of cases), banking and finance (13 percent) and chemicals (12 percent). But few sectors have escaped the attention of IP thieves.
Given those stakes, mitigating even one act of IP theft could pay huge dividends to an organization, not just financially but also legally, operationally and reputationally.
Take the first step in transforming your cybersecurity program
Enterprise security teams are adapting to meet evolving business needs. With six global Security Operations Centers, emerging technology partners and a dedicated team of security specialists, Cyderes is well-positioned to be your organization’s trusted advisor in cybersecurity. We’ll help you understand your risk exposure, increase your visibility and ROI, and proactively hunt for the latest threats.
