Article contributed by Joel Rader, Solutions Architect & Chris Thomas, Sr. Security Consultant
If there weren’t enough attack vectors to worry about for cybersecurity threats, keep in mind you should also take inventory of any cranes in which you interact. Turns out cranes just might be an avenue for cyber-attacks, as called out in this recent DHS Fact Sheet on Cybersecurity within Maritime Critical Infrastructure. While addressing the concerns around the PRC-manufactured Ship-to-Shore cranes, it is noted that port authorities are directed to report any cyber threats involving maritime cyber infrastructure. Additionally, there are call outs for preventing access to infrastructure for unapproved entities as part of the primary recommendations made by officials. Not just cranes, but all devices are within the scope of the recommendations.

But what exactly does a hacked crane, or any other device look like? And what if the device can't be easily replaced or bypassed? Protecting critical infrastructure like ship-to-shore cranes is just one example of an important item. There have been other recent cyber-attacks on critical infrastructure, such as the denial-of-service attack on this water treatment facility in PA. In this case, the primary target for exploitation was a Programmable Logic Controller (PLC). In case you don't know what these devices look like, here's an example from Wikipedia.
 Programmable Logic Controller (PLC)
Programmable Logic Controller (PLC)
As you can see, it's not immediately obvious how to implement the following "Actions to Take Today" advice from CISA on a PLC device shown below. These actions list a set of best practices to remediate [exploited PLCs across multiple critical sectors]:
- Implement multi-factor authentication (MFA)
- Use strong, unique passwords
- Check PLCs for default passwords
To be fair, the device in this particular CISA report looked more like what is better described as a "Human Machine Interface", like the device pictured below. These HMIs can be thought of as minicomputer terminals with various amounts of interactions exposed, often via a touchscreen interface.
Given the level of complexity associated with these devices, I don't think any Cybersecurity professional will be surprised that such a device like this could be used for a cyberattack. Just because there isn't an obvious interface (like an admin web page or touchscreen), doesn't mean there isn't a hidden/remote interface that needs securing as well. Thankfully, these devices are often secured behind physical boundaries, preventing straightforward access. Defense-in-depth is extremely important in all critical infrastructure, as some devices cannot rely on a pure "cybersecurity" approach to protect access. Physical boundaries are important to maintain and monitor.
 Human Machine Interface (HMI)
Human Machine Interface (HMI)
From an IAM Professional's Perspective
Now, from an Identity and Access Management (IAM) perspective, the recommended actions by CISA are straightforward to understand. Let's take a look at the first bullet: Implement Multi-factor Authentication (MFA). That... isn't a straightforward implementation no matter where you're at in the MFA journey.
We have many tools at our disposal in order to augment the lowly password in our Authentication workflow. There is a wealth of options in order to prove the standard options for Something You Know, Something You Have, and Something You Are in an MFA token scenario. However, many of the form factors that these tokens take present challenges in the Critical Infrastructure/OT environment. As one example, any MFA token that requires physical issuance can present a huge challenge in deployment timeframes. What about physical backups of the token itself? Depending on the environment and business parameters there can be a lot of unique factors that must be considered before implementing MFA can realistically begin.
The other two recommendations - use strong, unique passwords and check for default passwords - are well understood in the IAM space, but often are looking at best practices around user accounts and not so much physical devices like PLCs/HMIs. There's a big difference in securing a logon portal to a SaaS application, versus a PLC that is controlling a critical valve in an electric generation facility.
To help put devices into perspective, here's a diagram that a Critical Infrastructure professional might use to describe how those devices fit into their environment:
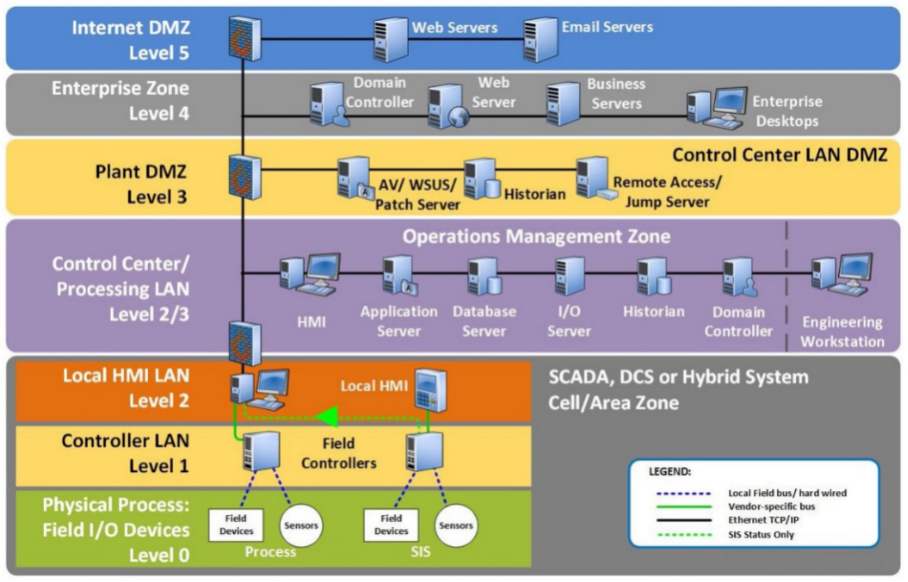 Perdue Enterprise Reference Architecture (PERA) model
Perdue Enterprise Reference Architecture (PERA) model
It looks like a reasonable layout, and there's certainly a lot of those callouts, such as the HMI devices callout (which can include PLC devices too). Essentially these are multi-function devices that have software interfaces that control critical devices, which will then have some method of human input exposed.
SaaS vs Critical Infrastructure
In the software world, especially in SaaS, there's a near-real time expectation of communication and availability. Downtime in user authentication or access can have impacts within seconds on high-traffic applications. Much of modern IAM is focused heavily on the "Confidentiality" component of the "CIA Triad" (Confidentiality, Integrity, and Availability). There are Federation protocols to remotely query a trusted partner's identity provider directory across the globe, determine the user's currently group listings, and then translate those permissions across the network and grant the user appropriate access. This workflow repeats itself throughout the day, and users are constantly providing various credentials for authentication to prove who they are. When you log into your company's enterprise applications, they are highly motivated to ensure they know exactly which user you are. As is your bank, email provider, and any other critical application.
This is however not so easy in a Critical Infrastructure environment! You may not even have access to a keyboard, much less a strong phishing-resistant MFA token such as a FIDO2 device. HMIs have limited interfaces and can be operational "black boxes" when it comes to their internal operating system (e.g. Windows). Applying modern IAM best practices is essentially impossible over the full scope of device that one would encounter in the field.
Instead of first focusing on implementing IAM best practices, it's important to understand why the ICS/OT environment is so different. Let me introduce Chris Thomas, an ICS/OT Security Consultant here at Cyderes who supports Critical Infrastructure clients.
Critical Infrastructure - Hands On
In speaking with Chris, I asked about how things are looked at from the “end-user” perspective in ICS/OT environments. What are some major differences in perspective when it comes to implementing Cybersecurity or IAM? What are some important considerations specific to those critical environments that need to be better prioritized? For example, the cornerstone of Information Security is the CIA Triad of Confidentiality, Integrity, and Availability. And within IAM, there are a wealth of options to help solve each of those points. However, in critical environments such as wastewater treatment facilities, any device that is not in proper functioning form can potentially be life-threatening. So, there is consideration of priorities that supersedes in many cases the standard approach an IAM professional might take.
CIA Triad isn't the same in ICS/OT:- Safety - Life and environmental safety are critical considerations.
- Reliability - Get the expensive process in operation, like right now!
- Integrity of Data (in operation) - Is the device operating properly (aka fail-safe otherwise).
- Confidentiality - Identity is kind of at this layer… meaning cybersecurity breaches earlier in history are hard to even detect.
Improving Critical Infrastructure with IAM
So, where's the overlap between IAM and Critical Infrastructure? Where do you start applying IAM best practices, but in a complicated real-world environment like Critical Infrastructure?
There's a lot of factors that need to be considered in a secure, fail-safe design. The more factors to consider, the more time it takes to architect a solution. Simultaneously, there are more active cyber threats all across the world every passing moment, nation-state hackers and otherwise.
So, time is of the essence! Plus, there's a limited amount of human resources available to help implement changes. Thankfully, with modern tooling, there are also a lot of avenues to solving cybersecurity challenges that simply weren't available years ago. Below are some resources that can provide additional background and specifics for critical infrastructure.
Cross Sector Cybersecurity Performance Goals - Recognizing the need for common language around multiple sectors, CISA has a useful guide that aligns with NIST's Cybersecurity Framework. These metrics prioritize investment in a limited number of essential actions with high-impact security outcomes.
Critical Infrastructure Sectors - 16 sectors are defined along with plans addressing their unique cybersecurity needs. These sectors also align with Presidential Policy Directive 21 (PPD-21), issued in 2013 addressing critical infrastructure systems.
North American Electric Reliability Corporation, Critical Infrastructure Protection (NERC CIP) link - Critical Infrastructure can span multiple countries, so cooperation is critical in addressing vulnerabilities.
The Value Cyderes Can Offer
Organizations today are facing more cyber threats and have to prioritize their limited resources to effectively triage those threats. Managed cybersecurity services, such as those offered by Cyderes, can provide numerous benefits specifically tailored to Critical Infrastructure environments. Here are some key advantages:
- Expertise and Specialization- Cyderes typically employs cybersecurity professionals with expertise in ICS/OT environments. These specialists understand the unique challenges, threats, and compliance requirements specific to critical infrastructure sectors. Leveraging their specialized knowledge, they can offer tailored solutions and recommendations.
- Continuous Monitoring and Threat Detection- Managed cybersecurity services continuously monitor ICS/OT networks for anomalous activities and potential security incidents. Using advanced threat detection technologies, such as intrusion detection systems (IDS) and security information and event management (SIEM) platforms, they can swiftly identify and respond to threats before they escalate.
- Rapid Incident Response - In the event of a security incident or breach, Cyderes can provide rapid incident response services. Their cybersecurity analysts are trained to quickly investigate and contain threats, minimizing the impact on critical operations. This swift response helps mitigate downtime and potential damage to physical assets.
- Compliance and Regulatory Support - Many industries, including those operating ICS/OT environments, are subject to strict regulatory requirements and standards. Managed cybersecurity services can assist organizations in achieving and maintaining compliance with relevant regulations such as NERC CIP, NIST SP 800-82, and ISA/IEC 62443. They can also help prepare for audits and provide documentation to demonstrate compliance efforts.
In summary, partnering with a reputable managed cybersecurity provider like Cyderes can enhance the security posture of IT/OT environments by providing specialized expertise, continuous monitoring, rapid incident response, regulatory support, scalability, access to advanced technologies, risk management, and 24/7 support. This enables organizations to focus on their core operations while effectively mitigating cybersecurity risks.