Cyderes has discovered a stored cross-site scripting (XSS) vulnerability within Vanderbilt REDCap, a web application that allows users to create and manage online surveys for research purposes.
In early July 2023, Cyderes observed that version 13.1.35 and below of REDCap allows a remote authenticated user to inject arbitrary code via a project creation functionality for registered users to build surveys. For each created project, there is an editable title field that does not filter input, and this makes it possible to inject malicious JavaScript and HTML into the application.
In terms of impact, the above issue could potentially be exploited to redirect users to a website controlled by malicious actors, which may ultimately lead to credential harvesting or downloaded malware.
Keeping with industry best practices, Cyderes contacted Vanderbilt to disclose this identified vulnerability. Vanderbilt began remediation immediately and promptly released a patched version (13.8.0).
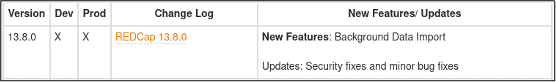
Figure 1: 13.8.0 version released with fixes
Disclosure Timeline for CVE-2023-37798
- July 5, 2023: Cyderes discovered vulnerability
- July 5, 2023: Cyderes informed vendor
- July 5, 2023: Vendor acknowledged and started fixing the bug
- July 6, 2023: Vendor informed Cyderes of fix release for July 7, 2023 (version: 13.1.37 LTS, 13.7.4 SR, 13.8.0 SR/new LTS version)
- July 6, 2023: Cyderes submitted a CVE request
- July 14, 2023: The CVE was assigned [on hold]
- Sep 6, 2023: Cyderes published this blog post
Technical Details
Affected Component
Version: 13.1.35 and below
Vulnerable parameter: Project title
Proof of Concept
Example payload: <image/src/onerror=alert(‘vulnerable_To_XSS’)>
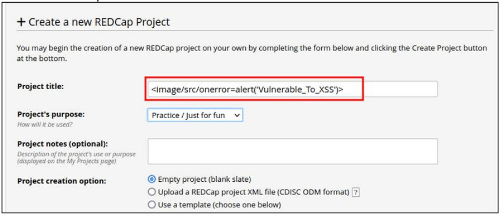
Figure 2: XSS payload
To execute the payload, simply click on the project title.
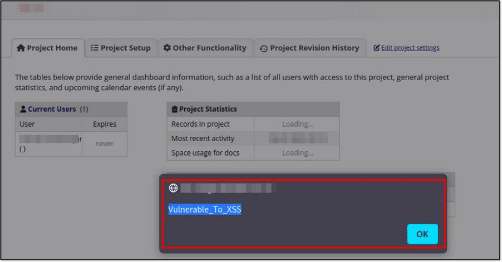
Figure 3: Payload execution
Recommendation
Any area of a web application that accepts and stores user input generally should not be trusted. Cyderes recommends taking appropriate measures to sanitize or encode data before being shown in a later browser response.
Credits
Special thanks to Michael Tomlinson for helping in the CVE request process.
By Mohit Kalsi
Mohit is a security consultant and pentester on the offensive security team at Cyderes. He has a keen interest in network and Active Directory pentesting, having journeyed through the realms of vulnerability management and walked the path of a SOC analyst in a past role. Passionate about cybersecurity, Mohit’s relentless curiosity not only keeps him synced with the latest threats and techniques; it drives him to approach security challenges from various angles to deliver effective solutions.
If you’re looking to contact one of our thought leaders, bolster your cybersecurity program, or just have a question feel free to reach out to us.
For more cybersecurity tips, follow Cyderes on LinkedIn and Twitter.



