This article was contributed by John Ayers, Vice President of Offensive Security at Cyderes.
As the IT security landscape gets wilder and woollier, companies are trying hard to stay one step ahead of cybercriminals and state actors, fortify their digital defenses and safeguard their valuable assets from potential breaches.
It will come as no surprise to most security pros that the strongest defense begins with an expertly planned and executed offense. And that’s precisely what the Cyderes Offensive Security team provides.
Cyderes Offensive Security offers a wide range of security services specifically tailored to improve your security posture. Cyderes cultivates and maintains relationships with best-in-class IT vendors, including developers of emerging and disruptive technologies. We pride ourselves on taking an IT-agnostic approach to solving clients’ challenges and needs.
A large component of what we do is reconnaissance and intelligence gathering. Day in and day out, we work with our clients to identify the myriad ways in which they may be vulnerable and provide seasoned counsel toward ‘plugging the holes’.
And while we have a tight focus on gathering vulnerability information pertaining to our clients’ attack surfaces (both technical and human), we also maintain a wider strategic gaze. We look at the bigger contextual picture and connect the dots, all the better to secure our clients’ respective fortresses most effectively.
The Rise of AI
It’s precisely that mindset that has allowed us to recognize the rise of GPT, and similar large language model-based generative artificial intelligence technologies, as a tech-seismic shift that is quickly and profoundly affecting multiple arenas: business/economic, political, cultural and, of course, technological.
To be sure, much benefit will come of AI, but this is where we instinctively and habitually broaden our perspective to see the full picture. Back to our forewarned/forearmed mantra: when we see something of this magnitude emerging, we certainly provide insights, but we also take measured and informed action. As we’re attuned to recognizing all-things-cyber-risky, we quickly have seen the potential threats this technology will present writ large.
Let’s say you’re a CISO. You’ve been losing sleep thinking about this new attack surface, counting shadows instead of sheep. Well, now you can rest assured, because Cyderes is actually doing something about it.
Enter Cyderes ACES (which stands for AI-Centric Security), our answer to the threats and challenges posed by fast, vast and bad terrain.
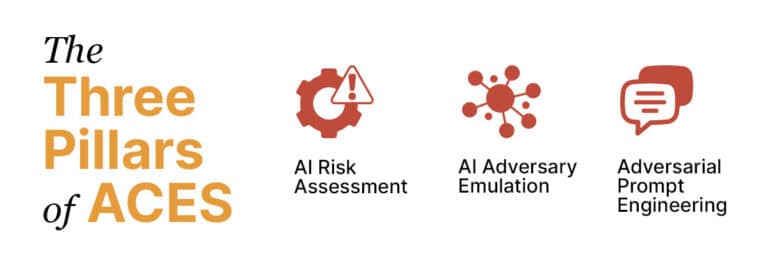
After assessing the emerging threat landscape, we have created three offerings that comprehensively cover interrelated cybersecurity issues (see diagram, above).
As a CISO facing this rapidly changing terrain, you need to be informed, educated and prepared to fight back against adversaries. The first offering within ACES arms you to do just that: we provide a bespoke AI Risk Assessment, which includes an ongoing analysis of proprietary intelligence addressing AI-leveraged and -enabled cybersecurity threats. We provide timely, vertical-specific intelligence that’s filtered, prepared and delivered at a tailored cadence alongside an actionable risk mitigation plan.
You also need to maintain your cybersecurity defensive chops, and that can only be done if you’re running up against simulations of the latest TTPs employed by threat actors. As the CISO, you can be confident that you’re receiving the most up-to-date, relevant and realistic AI Adversary Emulation against your environment, resulting in an associated mitigation plan from a trusted advisor.
We’ve also considered the needs of organizations that have large-language-model (LLM) development efforts underway. Through Adversarial Prompt Engineering, we execute adversarial actions focused against LLMs deployed in the organizational environment. From there, we provide risk identification and prioritization associated with the client’s LLM assets. In such cases, we help the CISO dodge the bullets of brand/reputational damage and organizational disruption and provide the tools to communicate risks to risk managers and stakeholders in a timely manner.
With these three offerings, Cyderes ACES enables you to be both forewarned and forearmed. We’ve got this, and we’ve got you. Contact us and we’ll take the next steps into this wild and woolly world together.
About the Author
John Ayers is Vice President of Offensive Security at Cyderes. John is seasoned security consultant with 20+ years of experience in cybersecurity managed services and consulting, practice and product management and marketing/sales enablement, and the author of numerous IT security articles, white papers and blogs.
Is your organization prepared for AI security threats?
Join our offensive security experts at Cyderes on July 26, 2023 at 11:00 AM CT for a panel discussion highlighting the ways that your organization can be prepared for the potential impacts, costs, and benefits of AI. Our panelists will delve into the specific ways that threat actors are using generative AI technology and how to best defend against those threats.
For more cybersecurity tips, follow Cyderes on LinkedIn and Twitter.



